AUTO NEXT
Show AllHide All
EPISODES:
Cryptography with Python 1: Introduction and content of course
Cryptography with Python 2: Cryptography & its classic security goals
Cryptography with Python 3: Confidentiality as a security goal
Cryptography with Python 4: Symmetric encryption with AES and ECB/CBC
Cryptography with Python 5: Using insecure AES-ECB in Python
Cryptography with Python 6: Using secure AES-CBC in Python
Cryptography with Python 7: Implementing AES in Python #1
Cryptography with Python 8: Implementing AES in Python #2
Cryptography with Python 9: Implementing AES in Python #3
Cryptography with Python 10: Implementing AES in Python #4
Cryptography with Python 11: Implementing AES in Python #5
Cryptography with Python 12: Implementing AES-ECB/CBC in Python #1
Cryptography with Python 13: Implementing AES-ECB/CBC in Python #2
Cryptography with Python 14: Asymmetric encryption with RSA
Cryptography with Python 15: Using RSA in Python
Cryptography with Python 16: Implementing RSA in Python #1
Cryptography with Python 17: Implementing RSA in Python #2
Cryptography with Python 18: Implementing RSA in Python #3
Cryptography with Python 20: Implementing hybrid RSA-AES encryption in Python
Cryptography with Python 21: Using EDH and ECDHE in Python
Cryptography with Python 22: Implementing a P-256 ECDHE in Python
Cryptography with Python 23: Integrity as a security goal
Cryptography with Python 24: Hash function structure and properties
Cryptography with Python 25: Hash function security
Cryptography with Python 27: Implementing SHA-256 in Python #1
Cryptography with Python 28: Implementing SHA-256 in Python #2
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cryptography with Python 26: Using MD5, SHA-1, SHA-2, SHA-3 in Python
Cryptography with Python 31: Using HMAC in Python
Cryptography with Python 34: Using AES-GCM in Python
Cryptography with Python 35: Implementing AES-GCM in Python #1
Cryptography with Python 36: Implementing AES-GCM in Python #2
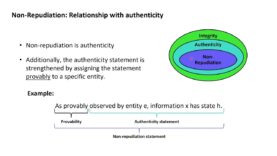
Cryptography with Python 37: Non-repudiation as a security goal
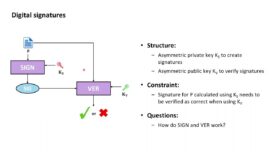
Cryptography with Python 38: Digital signatures
Cryptography with Python 39: Using RSA-PSS & Ed25519 signatures in Python
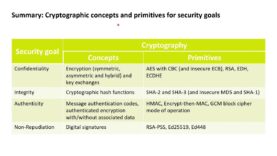
Cryptography with Python 40: Recap and summary